ZOS Compute System: Technical Architecture & Implementation
This document provides a comprehensive technical explanation of how the ZOS compute system works, detailing the architectural principles, implementation mechanisms, and technical innovations that enable its distributed computing capabilities.
Core Architectural Principles
ZOS is built on three fundamental architectural principles that differentiate it from conventional operating systems:
-
Autonomy: The system operates without requiring remote or local maintenance by system administrators, essential for a globally distributed grid architecture.
-
Simplicity: The operating system implements a minimalist architecture with only essential components, reducing complexity and enabling universal deployment with minimal resource requirements.
-
Stateless Design: ZOS instances maintain no persistent local state, ensuring system stability despite individual node failures by storing state information within the grid itself.
These principles create the foundation for a resilient, distributed cloud computing infrastructure that can scale globally while maintaining security, efficiency, and reliability.
System Architecture Overview
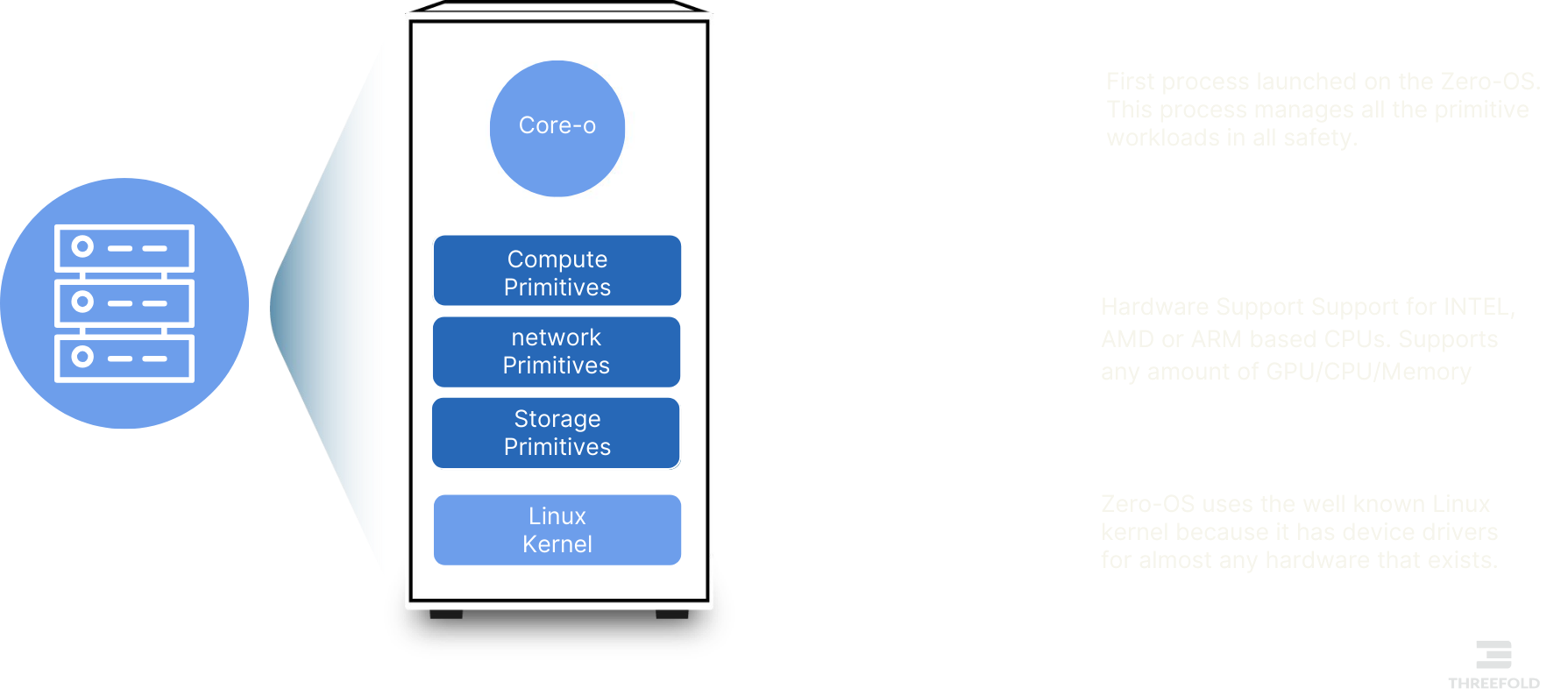
ZOS Core Components
ZOS implements a minimalist design philosophy, supporting only essential primitives that handle fundamental system functions:
- Compute Capacity Management: Allocates and manages computing resources through lightweight virtualization techniques
- Storage Capacity Management: Implements advanced file deduplication and distributed storage mechanisms
- Network Capacity Orchestration: Provides secure overlay networking capabilities with cryptographic verification
The system integrates these primitives with several compatibility features:
- Docker container support
- Virtual Machine (VM) compatibility
- Linux workload support
- Integrated distributed storage and network primitives
- Smart contract integration for IT resource allocation
Distributed IT Capacity Architecture
The ZOS distributed architecture generates compute, storage, and network capacity resources through several key components:
Compute Components
- ZKube: A specialized Kubernetes deployment architecture optimized for distributed environments
- ZVM: Container or virtual machine runtime environment providing isolated execution environments
- CoreX: Optional process management system offering secure remote access to ZVM instances
Storage Subsystems
- ZOS Filesystem: Deduplication-enabled filesystem replacing traditional container images
- ZOS Mount: SSD-based mounted storage location optimized for high-performance I/O operations
- Quantum Safe Filesystem: Distributed storage architecture implementing data integrity protection against loss or corruption
- ZOS Disk: Virtual disk technology available to OEM integration partners
Network Connectivity Architecture
- Mycelium Network: Globally distributed overlay network with client implementations for major platforms
- ZOS Router: Direct connection to public IP address space
- Web Gateway: Secure proxy architecture enabling controlled internet traffic routing to isolated instances
Deployment & Bootstrapping Process
Zero-Install Architecture
ZOS implements a network boot architecture that delivers the operating system to nodes over the internet, eliminating local installation requirements:
- Hardware Deployment: Compatible hardware is deployed at the desired location
- Resource NodePool Configuration: The system is registered on the grid explorer interface
- Bootloader Configuration: A minimal bootloader is implemented via USB media or network boot
- Network Initialization: Internet connectivity is established and hardware powered on
- Boot Sequence: The system automatically retrieves ZOS components from the network
The technical implementation involves:
- Optional Security Enhancement: Secure boot parameters in system BIOS
- Optional Cryptographic Verification: Signing certificates in BIOS for verified bootloaders
- Bootloader Retrieval: The bootloader is obtained from the content delivery network
- Core Initialization: The primary boot process (Core-0) initiates and performs self-verification
- Metadata Verification: Required software modules are cryptographically verified
- Service Initialization: The Core-0 zero image service initializes for container management
This approach enables a stateless architecture where the operating system runs without installation on local storage media, significantly enhancing security and deployment efficiency.
Workload Execution & Management
MyImage Architecture
A key innovation in the ZOS compute system is its approach to container and VM images:
Technical Implementation:
- The ZOS or Zero-Image CLI receives instructions to provision a virtual filesystem based on a Zero-Image URL reference
- Zero-Image metadata is stored on S3-compatible storage or specialized MyImageServer infrastructure
MyImage Technical Architecture: This implementation introduces a new image format that decouples image data from metadata:
- Comprehensive file descriptions include size parameters, timestamps, and POSIX attributes
- Each component contains a cryptographic fingerprint for deterministic execution verification
- Independent management of metadata and data components provides deployment flexibility
Quantitative Comparison:
- A standard Ubuntu image typically requires ~2 GB of storage and contains millions of files
- The equivalent MyImage metadata structure requires less than 2 MB (1000x reduction)
- The architecture downloads only required files, reducing transfer volume by ~10x
- All components undergo cryptographic verification before execution
Technical Advantages:
- Prevention of image tampering through cryptographic verification
- 10-100x reduction in storage and bandwidth requirements
- Potentially faster initialization for containers and VMs
- Deterministic execution with precise deployment parameters
- Compatibility with existing standards, Docker containers, and virtual machines
Deterministic Deployment Architecture
The ZOS compute system implements a deterministic deployment process as part of its Smart Contract for IT framework:
Technical Implementation Process:
-
Application Development: Code is compiled in a reproducible manner (same code always produces same binary).
-
Image Transformation: CI/CD pipelines convert above compule step or optionally Docker builds or other container formats into Zero-Image format
-
Workload Specification: Comprehensive parameters define network topology, gateway configurations, compute requirements, and resource allocations
-
Cryptographic Registration: Workload specifications receive cryptographic signatures using private key authentication
-
Distributed Detection: Infrastructure nodes implementing the ZOS protocol detect new deployment requirements through distributed consensus
-
Automated Deployment: Nodes retrieve verified workload specifications and initiate the deployment sequence
-
Integrity Verification: Each deployment phase undergoes cryptographic verification by ZOS to ensure specification compliance
Technical Advantages:
- Eliminates runtime dynamic behavior during deployment
- Ensures consistent and reproducible outcomes across environments
- Enforces complete file and configuration definition at the filesystem list level
Smart Contract for IT Clarification
Smart Contract for IT uses TFChain (ThreeFold blockchain) for deployment verification and management. It is separate and distinct from MyLedger, which handles identity management. See TFChain documentation for blockchain details.
Smart Contract for IT
The deployment of IT workloads is implemented through a decentralized architecture utilizing distributed ledger technology:
Key Technical Capabilities:
-
Multi-Signature Authentication Protocol: Workload deployment requires cryptographic signatures from multiple authorized entities before execution, implementing consensus-based deployment that prevents unilateral control
-
Immutable Deployment Architecture: Upon verification, workloads execute according to smart contract parameters with:
- Protection of deployed workloads and data from all parties
- Cryptographic verification of the deployment process
- Immutable transaction recording on the distributed ledger
-
Autonomous Management Agents: Virtual system administrators implement predefined operational protocols for maintaining compliance with specified parameters
-
Geo-Aware Distributed Ledger Integration: All transaction details are cryptographically registered, creating a permanent, tamper-resistant deployment record
This technical architecture ensures IT workloads are deployed with cryptographic security, protected against unauthorized modification, and operate within a decentralized, autonomous framework.
Distributed Hub Architecture
The ZOS compute system implements a horizontally scalable distributed infrastructure through its hub architecture:
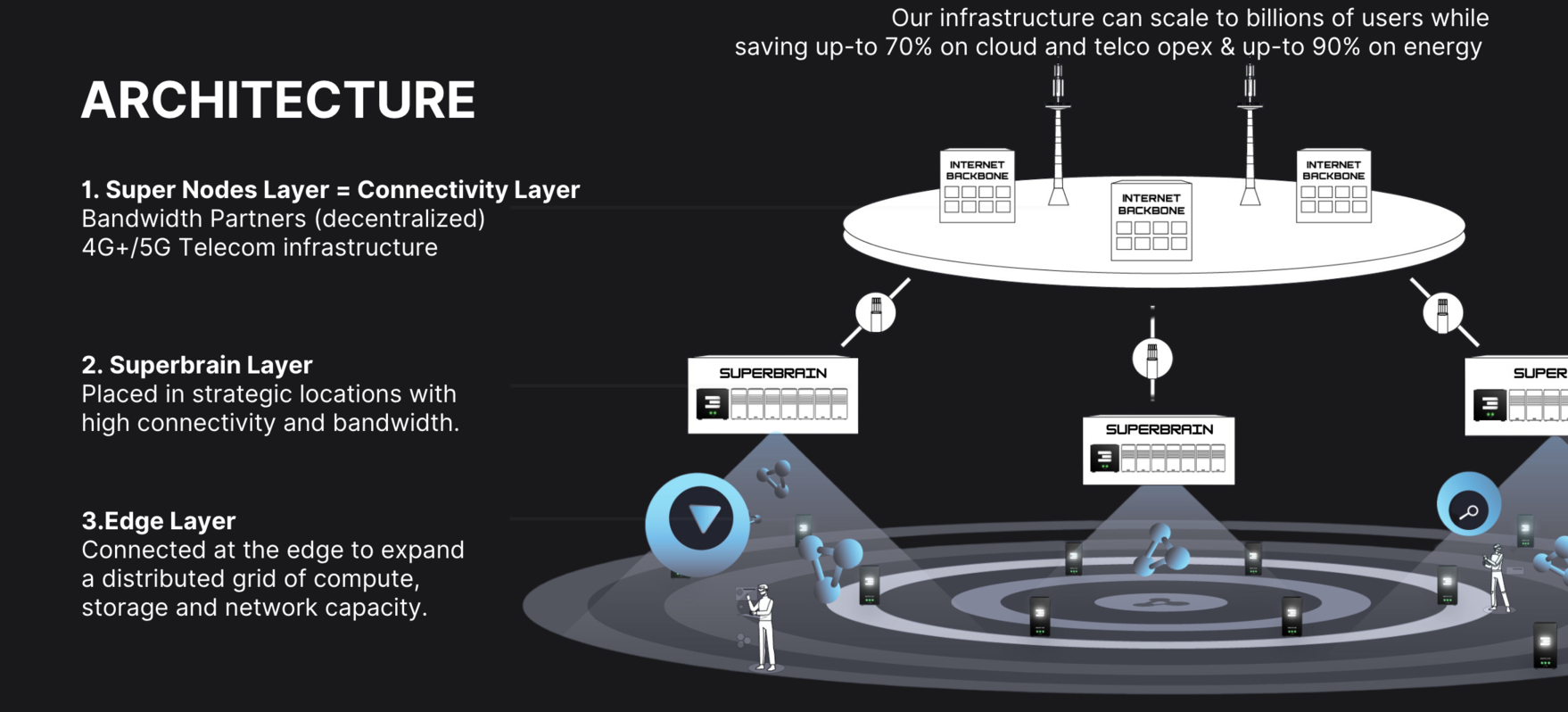
This architecture enables geographic distribution of compute resources while maintaining efficient workload deployment and management across the entire network.
Energy Efficiency Architecture
The distributed nature of the ZOS compute system inherently enables significant energy efficiency improvements:
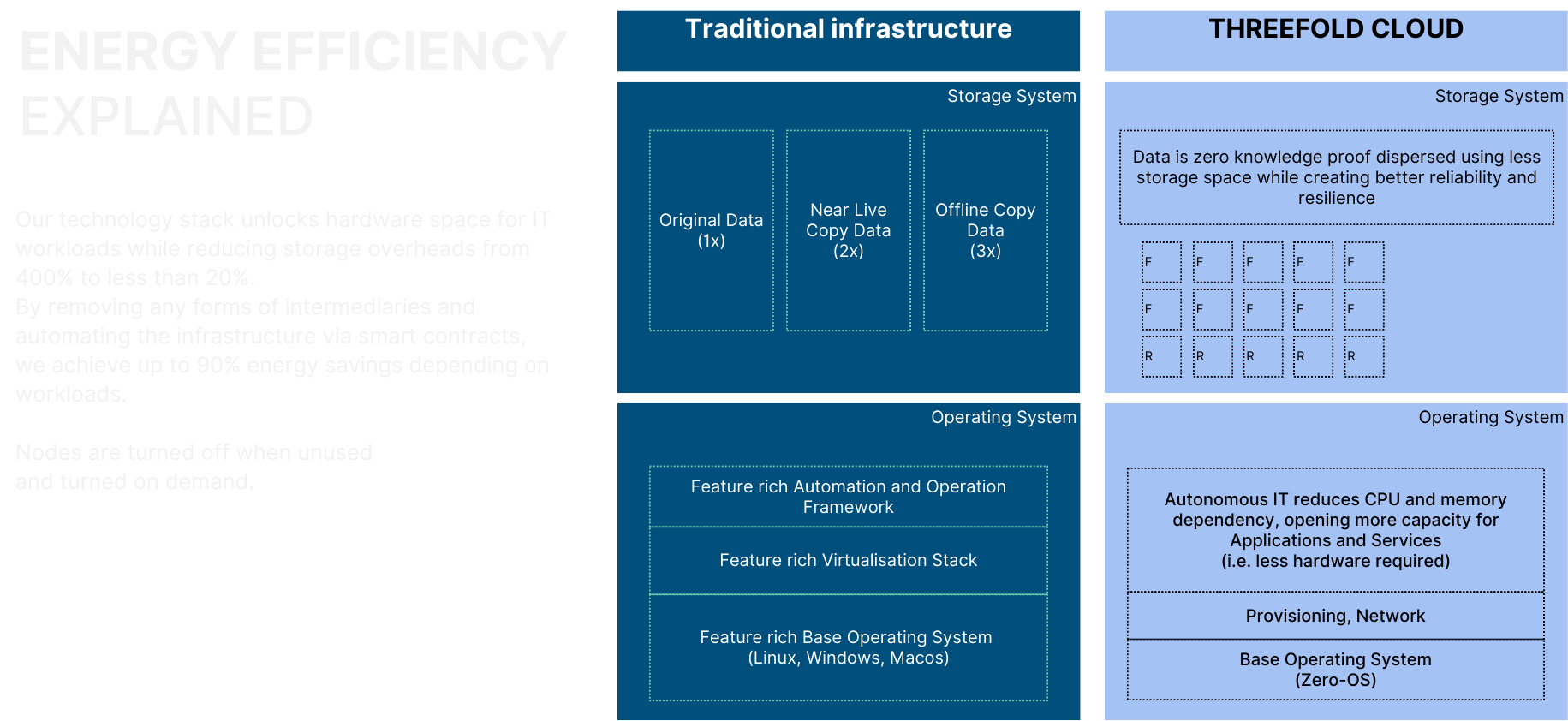
Technical Approaches:
- Decentralized peer-to-peer infrastructure implements path optimization algorithms
- Shortest route identification between endpoints reduces data transmission distance
- Lower power requirements for network infrastructure
- Workload proximity to data sources minimizes unnecessary data movement
Benchmark testing indicates this architectural approach can achieve up to 10x energy efficiency improvements depending on specific use cases and deployment scenarios.
Security Architecture
The ZOS compute system incorporates security at every level of its architecture:
-
File Integrity Verification: Cryptographic fingerprinting verifies application integrity before launch
-
Reduced Attack Surface:
- No shell or server interface exposed in the operating system
- End-to-end encrypted network communication between nodes
- Network/compute isolation architecture separating compute/storage from network services
-
Container Isolation: Enhanced security through dedicated virtual machines for container execution
-
Autonomous Operation: Reduction of attack vectors by eliminating human error potential
-
Cryptographic Verification: All deployment phases undergo verification to ensure specification compliance
-
Immutable Execution Records: Transaction details are cryptographically registered on a distributed ledger
This comprehensive security approach creates a robust foundation for high-security computing workloads.
Technical Comparison with Conventional Approaches
| ZOS Compute Architecture | Conventional Approaches | |
|---|---|---|
| Management | Distributed peer-to-peer architecture with autonomous agents and blockchain-based IT contracts | Centralized management systems (e.g., Kubernetes) |
| OS Deployment | Stateless implementation with no local storage requirements | Image deployment or installer execution on physical hardware |
| OS Updates | Modular, deterministic rolling upgrades with decentralized distribution | Complex update processes with potential security vulnerabilities |
| Integrity Verification | Cryptographic verification prevents execution of modified files | Limited integrity verification, susceptible to man-in-the-middle attacks |
| Scalability | Horizontally scalable distributed architecture | Capital-intensive scaling requiring significant infrastructure investment |
| Security | Architecture optimized for high-security use cases | Complex security implementation with significant resource requirements |
| Energy Efficiency | Optimized architecture reduces power consumption by up to 10x for specific workloads | Higher power consumption due to architectural inefficiencies |
| Liquid Cooling | Compatible with liquid cooling due to autonomous operation without hardware replacement requirements | Implementation complexity due to maintenance requirements |
| Autonomy | Self-managing architecture | Typically requires active management |
| Operational Complexity | Simplified deployment model accessible to non-specialists | Requires specialized expertise |
System Implementation Status
The core ZOS compute system technology has been in production use for multiple years, with ongoing development and enhancements to expand capabilities:
- ZOS Core: Production implementation
- MyImage Architecture: Production implementation
- Zero-Install Architecture: Production implementation
- Smart Contract for IT: Available for OEM (special contracts), general availability in ZOS v4 release (H2 2025)
- Deterministic Deployment: Available for OEM, general availability in ZOS v4 release (H2 2025)
Conclusion
The ZOS compute system represents a fundamentally different approach to cloud infrastructure, implementing architectural principles that address the limitations of conventional centralized models. By focusing on autonomy, simplicity, and stateless design, the system delivers superior security, efficiency, and resilience while enabling truly distributed computing at global scale.
Its technical innovations in areas such as image management, deployment processes, and infrastructure orchestration create a solid foundation for next-generation computing workloads, particularly in scenarios requiring high security, geographic distribution, or energy efficiency.
The integration of distributed ledger technology through Smart Contract for IT further enhances these capabilities by providing cryptographic verification, immutable deployment records, and multi-signature authentication protocols that prevent unilateral control and ensure verifiable execution of workloads across the distributed infrastructure.