What do we Do
What do we do?
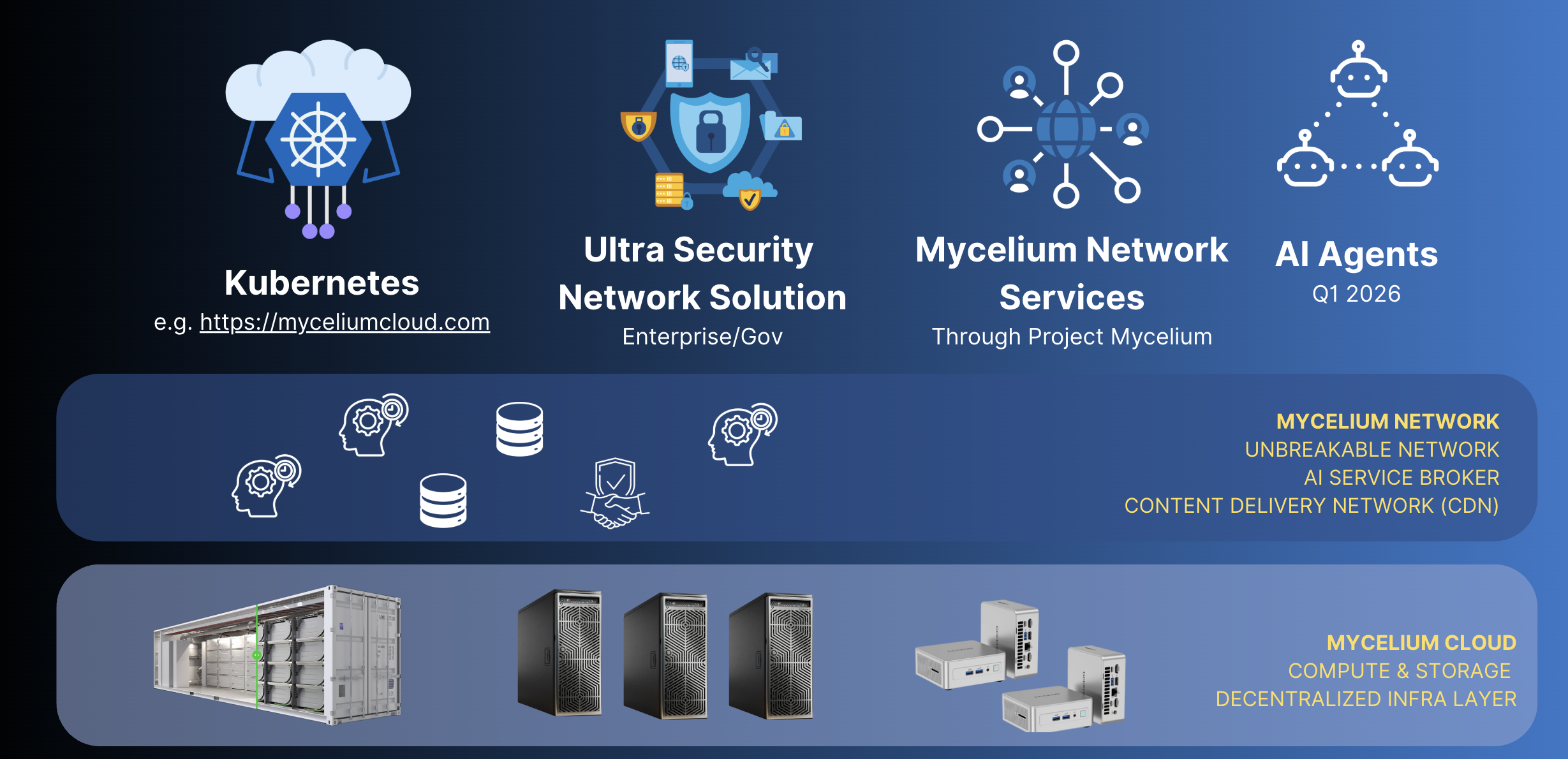
A truly reliable Internet requires fundamentally better systems for networking (communication), storage (data), and compute.
Mycelium has built these core technologies from the ground up, enabling anyone to become an infrastructure provider while maintaining autonomous, self-healing services covering all three fundamental layers of internet architecture.
Authentic, Secure & Globally Scalable Network Technology
- Our Mycelium Network technology enables seamless, private communication between people and machines, anywhere in the world, using the most efficient path available.
- It integrates with a global edge network of ultra-connected, low-latency supernodes to deliver superior performance and resilience.
- Mycelium is designed to overcome the limitations of the traditional Internet, such as unreliability, poor performance, and security risks.
- It provides core services including Naming, Shortest Path Routing, End-to-End Encryption, Authentication, a Secure Message Bus, and Content Delivery.
Data Storage & Distribution
- Our Quantum-Safe Storage system enables users to store unlimited amounts of data with full ownership and control.
- As soon as data leaves the application or compute layer, it is encoded in a way that is resistant even to quantum-level attacks.
- Users have full control over data availability, redundancy, and geographic placement.
- The system supports multiple interfaces, including IPFS, S3, WebDAV, HTTP, and standard file system access.
- Data can never be corrupted, and the storage system is self-healing by design.
Secure Compute
- Self-Managing & Stateless: Requires no manual interactions, enabling fully autonomous operation across global infrastructure.
- Secure & Deterministic Deployments: Every workload is cryptographically verified and deployed with guaranteed consistency—no room for tampering or drift.
- Efficient Deployment Storage System (Zero-Image): Achieves up to 100x reduction in image size and transfer using a unique metadata-driven architecture.
- Compatible: Runs Docker containers, virtual machines, and Linux workloads seamlessly.
- Smart Contract-Based Deployment: Workloads are governed by cryptographically signed contracts, ensuring transparent, tamper-proof deployment and execution.
Compare
| Feature | Others | Mycelium Tech |
|---|---|---|
| Deterministic Deployments Possible, no one (hacker) can alter state. | NO | YES |
| Autonomous/Self Healing Infrastructure which can scale to the planet. | NO | YES |
| Usable for any web2, web3 workload, compatible with now & future. | NO | YES |
| Data is geo-aware, war & disaster proof. | NO | YES |
| Can work in hyperscale datacenters as well as at edge. | NO | YES |
| Cost effective, can be 3x less | NO | YES |
| Networks can always find the shortest path and work over multiple media e.g. satellite, std internet, meshed wireless, lorawan, etc all end to end encrypted. | NO | YES |